© 2026 InterSystems Corporation, Cambridge, MA. All rights reserved.Privacy & TermsGuaranteeSection 508Contest Terms
InterSystems Security Contest
15 Nov, 2021, 12:00:00 AM - 05 Dec, 2021, 11:59:59 PM EST
The contest has already ended Topic
Technology bonuses
Sample applications
Who can participate
How to apply
Prizes and nominations
Terms and conditions, rules and judgment criteria
Winners
In the security contest, we encourage developers to share the solutions that show how to perform security tasks related to InterSystems IRIS and InterSystems IRIS for Health. We invite you to contribute apps that will reveal tasks related to the Authentication and Authorization parts of InterSystems Security Model
Here are the requirements:
- Accepted applications: new to Open Exchange apps or existing ones, but with a significant improvement. Our team will review all applications before approving them for the contest.
- The application should work either on InterSystems IRIS Community Edition or on InterSystems IRIS for Health Community Edition or on InterSystems IRIS Advanced Analytics Community Edition.
- The application should be Open Source and published on GitHub.
- The README file to the application should be in English, contain the installation steps, and contain either the video demo or/and a description of how the application works.
14 Registered Application(s)
Experts
 Filter
Filter Bonuses 


66Experts137Community
iris-disguise
Data Anonymization tool for InterSystems IRIS

55Experts142Community

zap-api-scan-sample
An example on how to scan your REST APIs on IRIS using the OWASP

46Experts90Community

iris-saml-example
InterSystems IRIS - SAML Authentication Test

40Experts95Community

API Security Mediator
InterSystems IRIS Declarative Security Rules for REST APIs

37Experts54Community

Data_APP_Security
OAuth Authentication, Authorization & Auditing basics

24Experts72Community

Server Manager 3 Preview
Now an Authentication Provider for VS Code, for better security

18Experts54Community
IRIS Middlewares
Specify your middlewares. security treatments on all requests.

14Experts35Community

isc-apptools-lockdown
Program for changing the security level of the system.

14Experts33Community

Audit Mediator
Object Script mediator to audit ObjectScript REST API requests

13Experts69Community
passwords-tool
Generating secure passwords and check strength of passwords

13Experts16Community
appmsw-dbdeploy
An example of deploying solutions with prepared databases, even without source code.

11Experts57Community
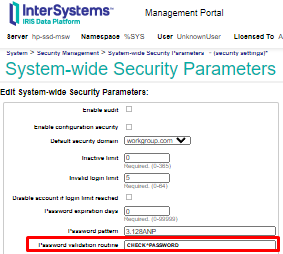
appmsw-forbid-old-passwd
To meet the requirements of section 8.2.5 PCI DSS "Prohibit the use of old passwords", a small application has been implemented that will be launched by the system when a user tries to change a password and check if it was used before.

5Experts34Community

https-rest-api
Rest API with Apache2 Web server

5Experts15Community

TimeTracking-workers
TimeTracking-workers









